When a company loses your data, data breach notification requirements are the rules that legally force them to tell you about it. These laws make sure you find out quickly, so you can take action to protect yourself from identity theft, fraud, or other headaches.
What Happens When a Company Loses Your Data?
Think of a company you do business with as a keeper of your "digital wallet." It doesn't hold cash, but it might have your name, email address, password, or even your credit card details. A data breach is what happens when that digital wallet gets stolen or exposed.
Unfortunately, this happens all the time—tens of millions of people are affected by data breaches every single year.
This guide will walk you through what happens next. We'll break down your rights, what to look for in a notification letter, and the practical steps you should take to lock down your digital life. The goal is to cut through the confusion and give you the confidence to act when your information is at risk.
The infographic below shows just how much sensitive information can be packed into that digital wallet, all of which can be exposed in a single breach.
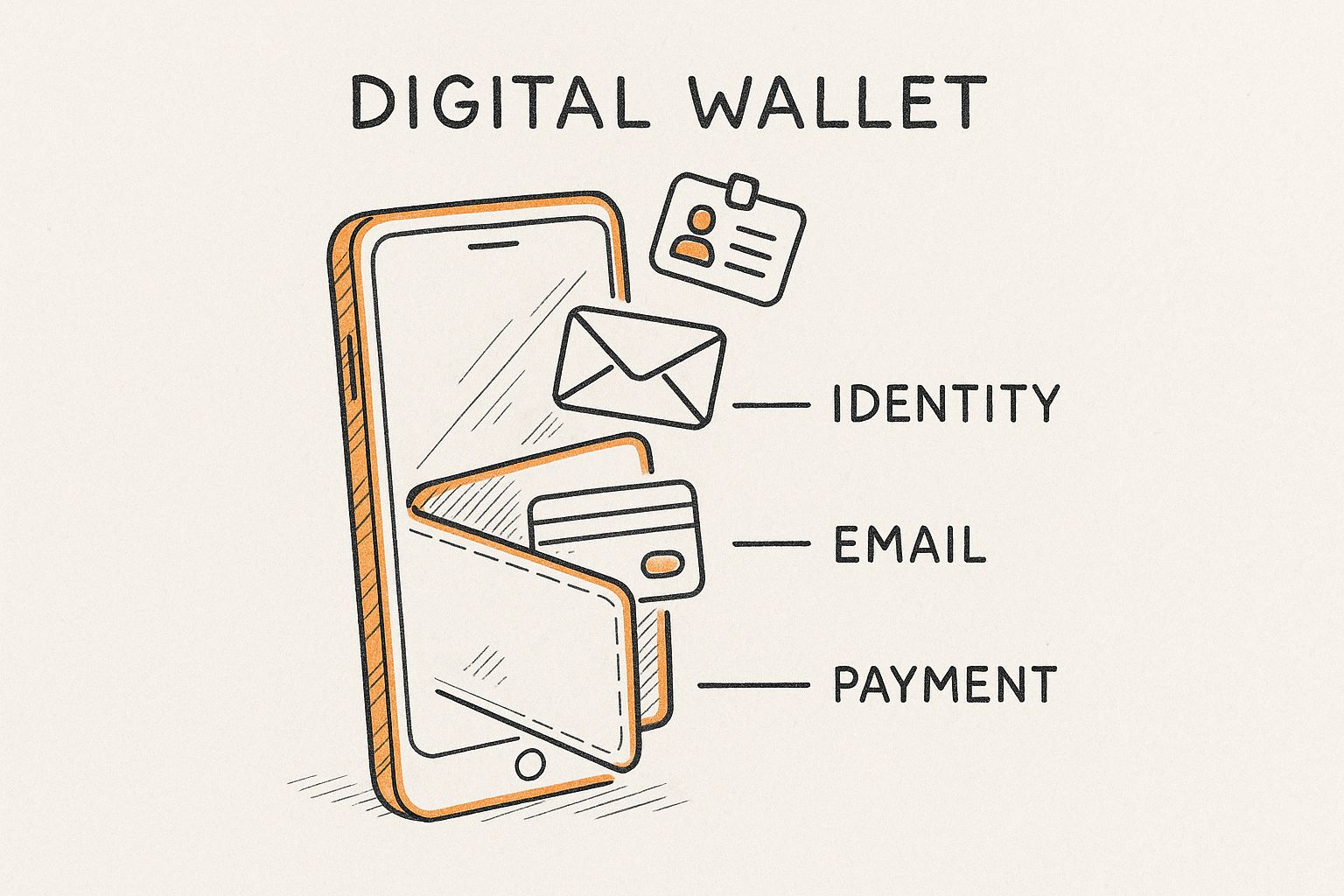
As you can see, a breach of one account can easily domino into exposing multiple parts of your identity at once.
Why Notification Rules Exist
Data breach notification laws are basically a consumer protection alarm system. They were created because companies used to sweep security incidents under the rug to avoid bad press and legal trouble. This left customers like you in the dark and vulnerable.
These rules shift the power back to you by forcing companies to be transparent. They create a clear set of responsibilities for any business that handles your data.
- You get a timely warning. The laws set deadlines, forcing companies to alert you "without unreasonable delay." Some places, like California, are even stricter, requiring notification within 30 calendar days of discovering a breach.
- You get helpful information. A proper notification can't just say, "Oops." It has to explain what happened, what data was stolen, and what the company is doing about it. This gives you the details you need to protect yourself.
- It holds companies accountable. The risk of hefty fines and legal action gives companies a powerful reason to invest in better security before a breach ever happens.
At their core, these laws exist to give you a fighting chance. When a company fails to protect your data, the rules make sure you get the information you need to defend your identity.
Taking Control of Your Digital Footprint
Ultimately, a data breach notification is your cue to take action. It's a signal to change your passwords, keep a close eye on your financial accounts, and watch out for phishing scams that might use your stolen info. The faster you respond, the better your chances of minimizing any potential damage.
Understanding these requirements is the first step toward becoming a more empowered consumer. If you’re worried about what personal information is already out there, you can start taking proactive steps today. A good place to start is our guide on how to remove personal information from Google, which can help you shrink your digital footprint.
Understanding Your Digital Rights Under Privacy Laws
Think of data privacy laws as your digital bill of rights. These rules are designed to give you power over your personal information and, just as importantly, hold companies accountable when they mess up and lose it.
Knowing the basics is key to understanding what you're owed when a data breach hits the news. At their heart, these laws create clear data breach notification requirements that force companies to come clean. They can't just sweep a hack under the rug and hope you never find out.
The Two Main Approaches to Privacy Law
When you look around the world, there are two major philosophies shaping data privacy, and they directly affect how and when you'll get that dreaded notification email.
- The Comprehensive Model: This is Europe’s approach, best known by the General Data Protection Regulation (GDPR). It’s like having a single, powerful rulebook that applies to everyone, no matter the industry. Under GDPR, a company often has to tell authorities about a serious breach within a razor-thin 72 hours of discovering it.
- The Sector-Specific Model: This is the system you'll find in the United States. Instead of one big federal law, there’s a "patchwork" of different state and industry-specific rules. Your rights can literally change depending on where you live and what kind of data was exposed.
This patchwork system can be a headache. A company might have one deadline for telling its California customers about a breach and a completely different one for its customers in Texas. But even though the timelines vary, the fundamental goal is always the same: give you a fighting chance to protect yourself from the fallout.
A Landmark Law That Started It All
The idea that you have a legal right to be told about a data breach is surprisingly new. The very first comprehensive law of its kind was California's Security Breach Information Act (SB 1386), which went into effect way back in July 2003.
This groundbreaking rule was simple but powerful: it required companies to inform people if their unencrypted personal data was stolen. That California law set a precedent that slowly but surely spread across the country. It took until 2018 for every single state to finally have its own notification law on the books.
Despite that progress, getting the full picture is still tough. As of 2025, only 14 U.S. states require that breach notifications be made public. That means a lot of incidents still fly under the radar. You can dig deeper into the history of these crucial consumer protections at the Privacy Rights Clearinghouse.
What Rights Do These Laws Actually Give You?
While the details can get technical, major privacy laws grant you a core set of rights that become incredibly important after a breach. These rights are usually spelled out in a company's legal documents, which is why it helps to understand what is a privacy policy and the promises it makes.
So, what are these rights in simple terms? The table below breaks down what key privacy laws guarantee when your data is on the line.
Key Consumer Rights Under Major Data Privacy Laws
| Consumer Right | What It Means For You | Example Law (Simplified) |
|---|---|---|
| The Right to Be Informed | A company has to tell you it's collecting your data, why it wants it, and how it plans to use it. This is the foundation of transparency. | Both GDPR and CCPA require companies to provide clear and upfront privacy notices. |
| The Right to Notification | If your personal data is stolen in a breach that could harm you, the company has a legal duty to tell you directly, often within a specific timeframe. | GDPR sets a 72-hour reporting deadline to authorities; many U.S. states use phrases like "without unreasonable delay." |
| The Right of Access | You have the right to ask a company for a complete copy of all the personal information it has stored about you. | Under CCPA, you can request your personal data twice in a 12-month period for free. |
| The Right to Deletion | You can tell a company to delete your personal information, and it has to comply unless it has a legal reason to keep it. This is often called the "right to be forgotten." | GDPR gives you a strong "right to erasure," letting you remove data that is no longer needed for its original purpose. |
These aren't just abstract legal ideas; they're practical tools you can use. They ensure that when a company’s security fails, you aren’t left in the dark.
That notification you receive is a direct result of these laws. It’s designed to arm you with the information you need to secure your accounts, monitor your credit, and stay one step ahead of potential identity theft.
Why Breach Notifications Are Sometimes Delayed
Ever get a data breach notice and wonder why it took months for the company to tell you? It’s a fair question, but the delay is rarely about hiding the truth. More often, it’s a sign of a painstaking process happening behind the scenes to get the facts right.
Think of it like a digital crime scene. When a company’s security team discovers a breach, they can’t just sound the alarm. They first have to act like forensic investigators to figure out precisely what happened, who was impacted, and how the attackers got in. This is critical—sending out a notice with half-baked information could cause unnecessary panic or, even worse, tip off the criminals.
Rushing to judgment helps no one. The goal is to provide information that is accurate and genuinely helpful, not just alarming.
The Investigation Phase
The moment a potential breach is detected, an intense internal investigation kicks off. The first priority is always to stop the bleeding—to contain the threat and prevent any further damage.
From there, security experts start piecing together the puzzle. They have to determine which systems were hit, what specific data was stolen, and exactly how many people are affected. This digital forensics work is what makes a breach notification meaningful.
The core challenge for any company is balancing the need for speed with the need for accuracy. A premature notification can be just as damaging as a delayed one if the details are wrong.
This investigative stage is almost always the longest and most complex part of the response, involving a deep dive into logs, network traffic, and other digital evidence.
Navigating the Ticking Clock of Legal Deadlines
While the internal team is digging for answers, the company’s lawyers are racing against a different clock: legal deadlines. These data breach notification requirements are a complex patchwork that changes dramatically based on where the victims live.
Europe's GDPR, for example, is famously tough. It often requires companies to notify government authorities within just 72 hours of discovering a breach. While this report goes to the government, not directly to consumers, it puts incredible pressure on the initial investigation to move fast.
Things are even more complicated in the United States, where there’s no single federal law. Instead, companies have to juggle a mess of different state rules.
- Vague Timelines: Many states use fuzzy language like "without unreasonable delay" or "in the most expedient time possible." This provides some wiggle room for a thorough investigation but can leave consumers waiting.
- Specific Deadlines: On the other hand, some states are tightening the screws. A newer California law, SB 446, now mandates a hard deadline of 30 calendar days to notify residents after discovering a breach.
These conflicting timelines mean a single company might have to notify customers in California long before they notify customers in a state with more flexible rules, adding yet another layer of complexity.
When Law Enforcement Gets Involved
There’s one more major reason for a delay: law enforcement. If the FBI or another agency is actively investigating the cybercrime, they can officially ask the company to hold off on making any public announcements.
Why? To avoid tipping off the bad guys. A public notice could give attackers a heads-up, allowing them to destroy evidence, go deeper into hiding, or launch fresh attacks. When this happens, a company’s legal duty to notify you is temporarily put on pause to help catch the criminals.
Ultimately, the gap between a data breach and the notification you receive is a delicate balancing act. Companies have to juggle a deep-dive investigation, a tangled web of legal deadlines, and cooperation with law enforcement—all while trying to give you the clear, actionable information you need to stay safe.
How to Read a Data Breach Notification Letter
Getting that official-looking email or letter about a data breach is never a great feeling. It’s easy to feel a surge of panic and confusion, but that notification is actually your first line of defense. Think of it less as an alarm and more as a toolkit—it gives you everything you need to start protecting yourself.
The trick is to decode it quickly. These notices are often drafted by lawyers and can be dense, but you only need to pull out a few key pieces of information to build a solid action plan. Once you know what to look for, that confusing letter goes from being a source of stress to a clear roadmap for securing your identity.
Find the Four Crucial Sections
Most breach notifications follow a standard template because data breach notification requirements legally dictate what companies have to include. You can usually just skim the document to find four critical sections that tell you the whole story.
- What Happened: This is the company's brief, and often vague, summary of the security incident. You’ll see phrases like "unauthorized access" or a "cybersecurity event." Don't get bogged down in the technical jargon here.
- What Information Was Involved: This is the most important part of the entire letter. Look for a specific list of the data types that were exposed. The risk you face is wildly different if they lost your email address versus your Social Security number.
- What We Are Doing: Here, the company explains the steps it's taking to contain the damage. This usually includes things like securing its systems and working with law enforcement.
- What You Can Do: This is your personal checklist. It will spell out recommended actions, like changing your password, monitoring your accounts, or freezing your credit. Pay very close attention to this section.
These four elements are the core of any notice. By focusing on them, you can cut through the legal fluff and get straight to what matters.
What Kind of Data Was Stolen?
The single most important detail in the entire notice is that list of stolen data. This tells you exactly how serious the situation is and what your next move should be.
Not all data is created equal. A breach involving your name and email address is an annoyance that probably means more spam in your inbox. But a breach involving your Social Security number is a major threat that could lead directly to identity theft.
Treat the "What Information Was Involved" section as your personal risk assessment. The data types listed there will determine whether you just need to change a password or if you need to take more drastic measures, like a credit freeze.
For instance, if the notice mentions financial information like credit card numbers was exposed, your first call should be to your bank. If it mentions login credentials, your immediate priority is changing that password—and the password on any other site where you've reused it.
Understanding the Offer of Free Credit Monitoring
Many data breach letters come with an offer for one or two years of free credit monitoring or identity theft protection. It’s natural to be skeptical of a "free gift" from a company that just lost your data, but in almost every single case, you should accept it.
These services are a valuable safety net. They watch your credit reports and send you alerts about suspicious activity, like someone trying to open a new credit card in your name.
Here's what these services usually provide:
- Credit Monitoring: You get alerts for new accounts, credit inquiries, or other major changes to your credit reports at the big three bureaus (Equifax, Experian, and TransUnion).
- Identity Theft Insurance: Many offers include an insurance policy to help cover the costs of recovering your identity, such as legal fees or lost wages.
- Restoration Services: If the worst happens, you’ll have access to specialists who can guide you through the painful process of reclaiming your identity.
Signing up is usually easy and gives you a powerful layer of protection at zero cost. The letter will include an enrollment code and a deadline, so make sure to act on it before it expires. That one simple step could save you a world of trouble down the line.
Why Some Data Breaches Go Unreported
You’d think any time a company has a security slip-up, a notification letter is legally required to show up in your mailbox. But the system is actually designed with specific thresholds to avoid causing mass panic over minor incidents that pose no real threat to you.
The law gets that not all data exposure creates the same level of risk. Data breach notification requirements are really only triggered by the likelihood of harm. If there’s no reasonable chance of your information being misused, a company may not have to send an alert at all.
When Is a Breach Not a Breach?
One of the most common reasons a breach goes unreported is because the stolen data is basically useless to criminals. The most powerful defense here is strong encryption.
Think of encryption like a digital safe. If a thief steals the safe but has no possible way to crack the code, the valuables inside are still secure. It's the same idea with your data—if a company loses an encrypted hard drive and the decryption key is safely stored somewhere else, your information is still unreadable and protected.
In this scenario, most laws agree that since the data is inaccessible and the risk of harm is extremely low, a formal notification isn't necessary. The whole point of these rules is to warn you about genuine danger, not every little technical glitch.
Likewise, if an incident involves a tiny number of people and the exposed information isn't sensitive—say, a publicly available list of business emails—it probably won’t meet the legal bar for a full-blown notification.
The Problem with Third-Party Breaches
Another huge factor that complicates things is the rise of third-party, or supply chain, breaches. This is when a company you trust doesn’t get hacked directly; instead, one of their vendors does.
Imagine you use a popular online store. That store uses a smaller company to handle its customer service emails. If that smaller email vendor gets hacked, it’s your data from the online store that’s exposed. The store you have a relationship with now has to rely on its vendor to investigate and share the details.
This creates a chain reaction that can seriously delay the notification you eventually get. In many cases, the original company may not even know about the breach for weeks or months.
This is a fast-growing problem. The share of breaches involving third-party vendors has been climbing, highlighting an urgent need for better coordination. Despite this, challenges remain, as less than a third of certain vulnerabilities were fully patched by organizations in the past year, leaving many businesses exposed. You can discover more insights in the 2025 Verizon DBIR to understand the full scope of these supply chain risks.
Ultimately, these exceptions are built into the law to make sure that when you do get a notification, it’s for a serious event that needs your immediate attention.
How AI Is Changing Breach Notifications
In the world of data security, technology cuts both ways. While criminals are using artificial intelligence to launch smarter and faster attacks, companies are now fighting fire with fire. Businesses are rolling out their own AI and automation tools to flip the script on cybercrime.
Think of it like an incredibly advanced digital alarm system. Instead of waiting for a security guard to spot a broken window, AI can detect an intruder the very second they step through the digital door. This near-instant detection is a total game-changer for data protection.
By catching threats earlier, companies can contain the damage much more quickly. This speed not only limits what criminals can steal but also cuts down the time it takes for a business to figure out what happened, who was affected, and how to fix it.
Shortening the Time to Notification
Ultimately, this technological arms race benefits you, the consumer. The faster a company can identify and contain a breach, the sooner it can meet its data breach notification requirements and get you the information you need. This speed is critical—it shrinks the gap between your data being stolen and the moment you're empowered to take action.
This isn’t just a theory; it’s already happening. A recent report from IBM shows these investments in AI and automation are paying off big time. According to their 2025 Cost of a Data Breach Report, the average time to identify and contain a breach has dropped to 241 days, a nine-year low. Even better, organizations that heavily use security AI were able to find and fix breaches a whopping 80 days faster than those without such tools. You can dive deeper into the numbers in the full IBM report.
AI-powered security acts like an early warning system, giving companies a crucial head start. For consumers, this means getting vital information sooner, reducing the window of opportunity for fraudsters to misuse your data.
Automation and the Future of Compliance
Beyond just detection, AI is also making the notification process itself much more efficient. Once a breach is confirmed, AI can sift through massive datasets to identify affected individuals in minutes, not days. It can even help draft clear, accurate notification letters that comply with the tangled web of state and international laws.
This kind of automation helps ensure that the notices you receive are both timely and accurate. As companies get better at handling the legal side of a breach, they can focus more on helping you, the customer. To see how automation is changing other legal workflows, check out our article on legal document automation software.
It’s a hopeful look at the future of data protection. While breaches are, unfortunately, here to stay, the growing use of AI means the response—and the critical notification you rely on—is becoming faster and more effective than ever before.
Common Questions About Data Breaches
Getting a data breach notification can be unsettling, to say the least. It’s easy to feel confused or overwhelmed. Let's walk through some of the most common questions and give you practical, no-nonsense advice on what to do next.
What’s the First Thing I Should Do After Getting a Breach Notification?
First, take a breath. Panicking won’t help. Read the notice carefully to understand exactly what kind of information was compromised, because that detail dictates your next move.
For instance, if a credit card number was exposed, your immediate priority is to call your bank and get that card canceled. If it was a password for an online account, you need to change it right away—and just as importantly, change it on any other site where you’ve reused it.
The single most important thing is to act on the specific information in the notice. Companies often offer free credit monitoring as part of the response. It’s almost always a good idea to sign up. Think of it as a free safety net.
How Can I Tell if a Breach Notification Is a Scam?
This is a great question because scammers love to piggyback on the fear caused by real data breaches. They’ll send out fake "breach" emails hoping to trick you into giving them your information.
A legitimate company will never ask you to click a link and enter your password, Social Security number, or other sensitive details to "verify your account." That’s a massive red flag and a classic phishing tactic.
To stay safe, just follow these simple rules:
- Never click on links in an email you’re not 100% sure about.
- Go directly to the source. Manually type the company’s official website address into your browser.
- Verify over the phone. Find the official customer service number on their website (not from the email!) and call to confirm if the breach is real.
Does a Data Breach Mean the Company Was Careless?
Not always. Today’s cyberattacks are incredibly sophisticated, and even companies with top-tier security can get hit. The fact that breach notification laws exist is a clear acknowledgment that breaches are a constant, unavoidable risk.
That said, if an investigation reveals the company was truly negligent—say, they ignored a well-known security flaw they should have patched or failed to implement basic, industry-standard protections—they could be in serious trouble. This often leads to hefty fines from regulators and lawsuits from the people whose data was exposed.
Can I Sue a Company for Losing My Data?
Yes, you absolutely can. Consumers frequently join together in class-action lawsuits after a major breach. To have a strong case, you generally need to prove that you suffered actual harm—like financial loss—as a direct result of the company’s failure to protect your data.
Some privacy laws are making this easier for consumers. The California Consumer Privacy Act (CCPA), for example, gives residents a clearer path to sue over certain types of data breaches. If you believe a breach has caused you significant damage, it might be worth speaking with an attorney who specializes in consumer privacy rights.
Dealing with legal notices and fine print is a headache. TermsEx uses AI to instantly break down privacy policies and terms of service, translating that confusing legal language into simple English. Protect yourself by actually understanding what you're agreeing to before a breach happens. Get your free analysis today at https://termsex.com.