Taking charge of your personal information isn't about becoming a cybersecurity genius. It’s about taking smart, simple steps to manage your digital footprint, secure your accounts, and be more mindful of what you share, both online and off.
It all starts with the basics: using strong, unique passwords for every account, turning on two-factor authentication wherever it’s offered, and taking a few minutes to check the privacy settings on the apps and websites you use every day.
Why Protecting Your Information Matters More Than Ever
In an age where almost every click, purchase, and "like" is recorded, your personal data has become incredibly valuable. We're not just talking about your name or email. This includes your browsing history, where you go, your financial records, and even your health information.
All these little data points, when pieced together, create a shockingly detailed profile of who you are, what you like, and how you live. Companies use this for targeted advertising, sure, but in the wrong hands, it can be used for much worse. Identity theft, financial fraud, and even personal manipulation are very real risks. The stress and financial fallout from a single data breach can drag on for years.
The Growing Concern for Data Privacy
You're not alone in worrying about this. Public concern over online privacy has never been higher, but there's a huge disconnect between being worried and knowing what to do.
In the United States, a staggering 92% of Americans say they are concerned about their privacy online. Yet, a tiny 3% claim to understand how current privacy laws actually work. That’s a massive gap between feeling anxious and feeling empowered.
This guide is here to close that gap. We're not going to bury you in legal jargon or complicated tech-speak. Instead, we'll give you a clear, actionable roadmap to help you understand and use key data privacy best practices.
The goal isn't to make you a security expert. It's about giving you practical knowledge to build a stronger shield around your digital life, one manageable step at a time.
What This Guide Will Cover
We've laid this guide out in a logical way, so each section builds on the last. By the end, you'll have a complete toolkit for keeping your personal data safe.
Here's a quick look at what’s ahead:
- Finding Your Digital Footprint: First, we’ll show you how to figure out exactly where your data is and who has it. It’s the essential first step.
- Building Your Defenses: Next, we'll get into the must-have tools, like password managers and two-factor authentication, that form the foundation of your digital security.
- Adopting Smart Habits: Then, we’ll explore the daily habits that make the biggest difference—from spotting phishing scams to simply thinking twice before you share.
- Using Your Legal Rights: Finally, you’ll learn how to use data privacy laws to ask companies to show you, correct, or even delete the information they have on you.
To give you a bird's-eye view of our strategy, here's a quick checklist summarizing the core areas we'll cover.
Your Personal Information Protection Checklist
This table breaks down the core strategies for protecting your personal data, highlighting the goal of each category and some practical actions you can take.
| Protection Category | Primary Goal | Key Action Examples |
|---|---|---|
| Data Auditing | Understand Your Exposure | Map your digital footprint, identify data brokers holding your info, review account permissions. |
| Technical Defenses | Secure Your Accounts & Devices | Use a password manager, enable two-factor authentication (2FA), encrypt sensitive files. |
| Behavioral Habits | Minimize Daily Risk | Spot and avoid phishing scams, use privacy-focused browsers, be selective about sharing data. |
| Legal Safeguards | Exercise Your Rights | Submit data deletion requests (CCPA/GDPR), opt out of data sales, review privacy policies. |
Think of this as your roadmap. Each part is crucial for creating a solid defense around your personal information. Let's get started.
Discover Where Your Personal Data Lives
Before you can protect your personal information, you have to know where it is. Think of it like securing your home—you wouldn’t just lock the front door while leaving all the back windows wide open, would you? A personal data audit is your way of checking every entry point. We're talking about every old account, forgotten app, and hidden data trail that makes up your digital footprint.
This process isn’t meant to make you paranoid. It's about empowerment. It gives you a clear map of your exposure so you can make smart choices about what to keep, what to delete, and what to lock down. It's staggering to think that 90% of all data in existence was created in just the last two years. That just shows how quickly our digital lives expand, often without us even noticing.
The infographic below breaks this down into a simple framework: Audit, Defend, and Act.
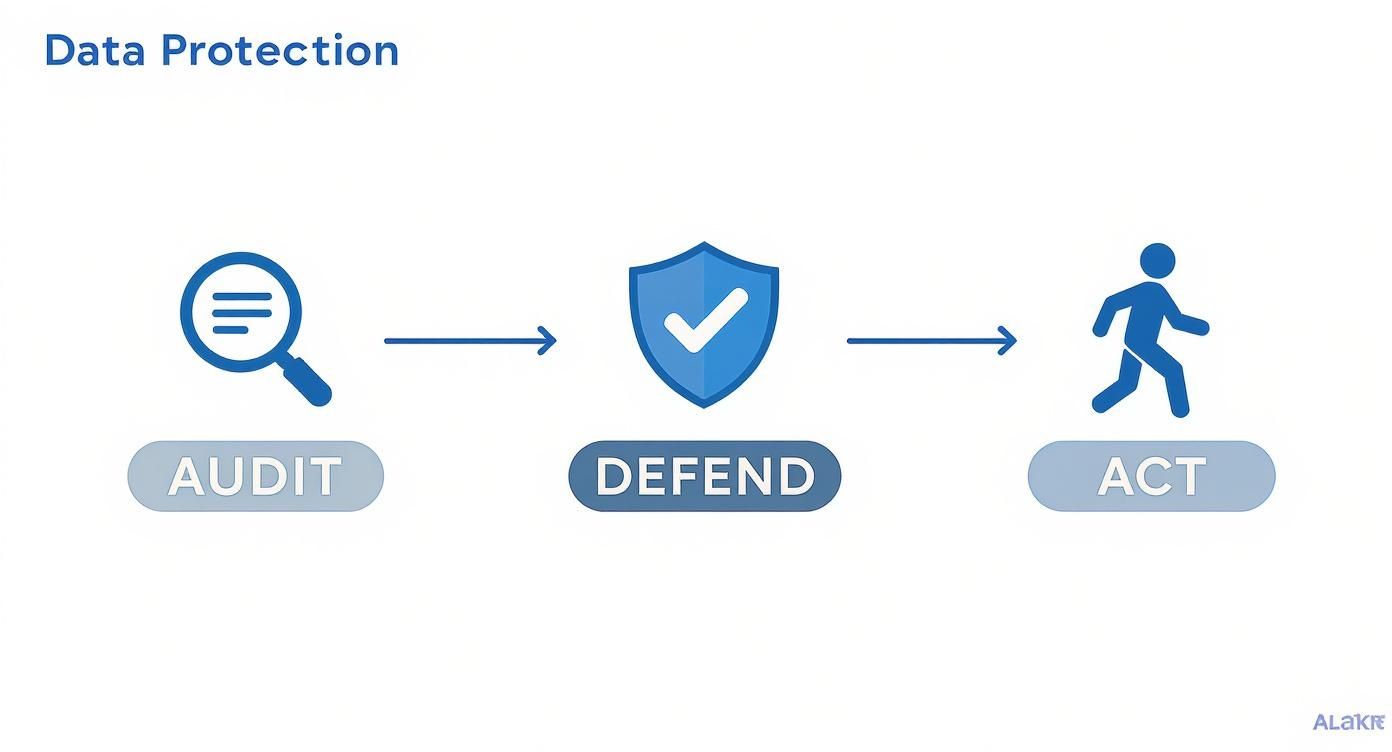
As you can see, finding your data (the Audit phase) is the bedrock. It’s the foundational step you have to take before you can build effective defenses and take real action.
Uncovering Your Digital Footprint
A great place to start is with the services you use every single day. The big tech companies actually have tools that give you a surprisingly detailed look at the data they’ve collected on you. These aren't just abstract settings; they're direct windows into your online behavior.
Take Google's "My Activity" dashboard. It's a running log of pretty much everything you do while logged into your Google account—your searches, the YouTube videos you watch, and even your location history if you have it on.
Seeing it all laid out can be a real eye-opener, and it’s the first step toward managing or deleting that history. In the same vein, Facebook has an "Off-Facebook Activity" tool that shows you which other websites and apps are sharing your activity with them. It’s often a much longer list than people expect.
Looking at these activity logs isn't a one-and-done task. Make it a habit to check them every few months. It helps you stay on top of your data exposure as you sign up for new services and download new apps.
Auditing Your Online Accounts
Beyond giants like Google and Facebook, think about all the other places you've created an account over the years. That online store you used once for a gift, the niche forum you joined in college, or that free photo editor you tried and forgot about—they all likely still have your data.
Here’s a practical way to find these forgotten accounts:
- Search your email inboxes: Dig through your old emails for terms like "Welcome," "Confirm your account," "unsubscribe," or "new account." You'll be surprised how many services you’ve signed up for.
- Check your saved passwords: Your web browser's password manager (or a dedicated one like LastPass or 1Password) is a goldmine for rediscovering old logins.
- Review social media logins: If you've used "Sign in with Google" or "Login with Facebook," check the security settings in those accounts. They'll have a section called "Apps with access to your account" that lists every service you've connected.
Once you have a list, the cleanup can begin. You can start deleting accounts you no longer need and tightening the privacy settings on the ones you want to keep. This audit is your first, most powerful move in learning how to protect personal information effectively.
Building Your Digital Fortress
Alright, you’ve mapped out where your information lives online. Now it’s time to build the walls and lock the gates. Knowing your data is out there is one thing; actively defending yourself is another. This is where we shift from looking to doing.
We're going to put the core tools and habits in place that will shield your most sensitive accounts from the most common cyberattacks. Think of these as your first and best line of defense. They work together, creating layers of security that make it so much harder for anyone to get into your digital life.
Master Your Passwords with a Manager
The old advice to "use a strong password" just doesn't cut it anymore. The real key to protecting your accounts is using a strong and unique password for every single site you use. It's a pain, we know, but reusing passwords—even complex ones—is a massive risk.
If one site gets hacked, criminals will take your leaked password and try it everywhere else. Your email, your bank, your social media... they're all vulnerable. This is precisely why a password manager is a must-have. Instead of trying to remember dozens of crazy passwords, you only have to remember one master password. The manager does all the hard work for you.
- It generates bulletproof passwords: Think long, random strings of characters that are nearly impossible to guess, like
J7#k&p!2sT@zV_9G. - It stores them securely: Your passwords are kept in an encrypted vault that only your one master password can unlock.
- It autofills them for you: This makes logging in a breeze and also protects you from phishing sites, since the manager will only fill in your details on the correct website address.
Honestly, getting a password manager is one of the single most important security upgrades you can make.
Enable Two-Factor Authentication Everywhere
Think of your password as the lock on your front door. Two-factor authentication (2FA) is the deadbolt. It’s that extra layer of security that requires a second piece of proof that you are who you say you are.
Even if a thief manages to steal your password, they can't get into your account without that second factor. Usually, it's something you have with you, like your phone.
Setting up 2FA might seem like a small hassle, but it stops the vast majority of account takeover attempts. It's the digital equivalent of a bank requiring both a key and a PIN to access a safe deposit box.
You'll run into a few different types of 2FA:
- SMS Codes: A code gets texted to your phone. It’s better than nothing, but it's vulnerable to "SIM-swapping" attacks where a scammer takes control of your phone number.
- Authenticator Apps: Apps like Google Authenticator or Authy generate a fresh, time-sensitive code right on your device. This is a much more secure method.
- Physical Keys: A small USB device (like a YubiKey) that you plug in to verify it's you. This is the gold standard for security.
Go turn on 2FA for every important service you use—especially email, banking, and social media. Do it today.
Keep Your Digital Doors Locked
Your software and browser are the doors and windows to your digital home. Companies regularly release updates not just for new features, but to patch security holes that hackers have found. Delaying those updates leaves you wide open.
Likewise, tweaking your browser's privacy settings can dramatically reduce how much data you leak just by surfing the web. You can add extensions that block trackers or use a VPN to encrypt your connection, which is a must on public Wi-Fi. If you're curious about how those services handle your data, our article on whether NordVPN keeps logs is a good place to start.
Smart Habits for Everyday Online Privacy
Having the right software is a great start, but the small decisions you make every day are what really build a fortress around your digital life. Protecting your personal information is just as much about your habits as it is about your apps. It's about weaving a privacy-first mindset into your daily routine until being cautious becomes second nature.
It all starts with mindful sharing. Before you post that photo, check into a location, or answer a fun-looking quiz on social media, just pause and ask yourself: does this really need to be public? Could it reveal where I live, what my daily schedule looks like, or the answers to common security questions?
For instance, posting vacation photos while you're still sipping cocktails on the beach is like putting a "Nobody's Home" sign on your front door. Sharing your pet’s name in a viral challenge might seem harmless, but if it’s also a password hint, you've just handed a key to a criminal. Taking a moment to review your privacy settings can make a huge difference. If you need a hand, our guide on adjusting your social media privacy settings is a fantastic place to start.
Spotting Scams Before They Strike
One of the most common ways people get their data stolen is through phishing. These are sneaky, fraudulent attempts—usually through email, text (smishing), or phone calls (vishing)—to trick you into giving up sensitive info. Scammers have gotten incredibly convincing, but they almost always leave clues.
They love creating a false sense of urgency, with messages claiming your account has been locked or you've won a prize that you must claim immediately. Look out for poor spelling, generic greetings like "Dear Customer," or email addresses that look almost right but have a slight typo.
Never click links or download attachments in a message you weren't expecting. The safest move is to open a new browser tab, go directly to the official website, and log in there to see if there are any real notifications waiting for you.
Phishing attempts prey on our tendency to act quickly without thinking. Knowing what to look for is your best defense.
The table below breaks down the common signs of a phishing attempt versus a legitimate message.
Phishing Red Flags vs Safe Communication
| Characteristic | Phishing Attempt (Red Flag) | Legitimate Message (Green Flag) |
|---|---|---|
| Sense of Urgency | "Your account will be suspended! Act NOW!" | Calm, informational language. "Your statement is ready." |
| Sender's Address | support@Pay-pal.com or amazon_support@mail.ru |
support@paypal.com or noreply@amazon.com |
| Greeting | "Dear Valued Customer" or "Hello Sir/Madam" | Uses your actual name. |
| Links | Hovering reveals a strange, unrelated URL. | Links go directly to the company's official domain. |
| Spelling/Grammar | Multiple typos and awkward phrasing. | Professionally written and proofread. |
| Attachments | Unexpected invoices, PDFs, or ZIP files. | Generally avoids attachments for routine notifications. |
Keep this checklist in mind next time an urgent-sounding email lands in your inbox. A few seconds of skepticism can save you a world of trouble.
Protecting Yourself in the Physical and Public World
Your privacy risks don't just vanish when you close your laptop. Simple offline habits are just as crucial for keeping your information safe.
Think about that free Wi-Fi at the coffee shop or airport. It's a huge weak spot. Without protection, anyone else on that same network could potentially spy on your online activity.
This is where a Virtual Private Network (VPN) is non-negotiable. A VPN creates a secure, encrypted tunnel for your internet traffic, scrambling it so it's unreadable to prying eyes. It’s the digital equivalent of sending your mail in a locked briefcase instead of on a postcard.
And what about all that paper? Bank statements, old bills, and pre-approved credit card offers sitting in your recycling bin are a goldmine for identity thieves. A cross-cut shredder is a small investment that pays for itself by making sure those documents are unreadable before you toss them.
This kind of vigilance is more critical than ever. Even with new regulations, data breaches are on the rise. In just the first six months of a recent year, there were 1,732 publicly disclosed data breaches in the U.S. alone. You can learn more about these global trends from DLA Piper's research on data breach costs.
You Have Rights: How to Use the Law to Protect Your Data
All the smart habits and technical tools in the world won't help you with one big problem: the data that companies already have on you.
This is where knowing your legal rights becomes a superpower. You can actually tell companies what to do with your information, and frankly, you have way more power than you probably realize. A wave of new privacy laws has given us specific rights to see, delete, and control the data businesses are holding. Think of them as a new set of tools for your privacy toolkit.
Know Your Fundamental Data Rights
While the specifics change depending on where you live, a few core rights form the backbone of modern data privacy laws. Getting a handle on these is the first step to legally protecting your personal information.
Two of the most powerful rights you have are:
- The Right of Access: This lets you go to a company and ask, "What personal information do you have on me?" They are legally required to give you a copy.
- The Right to Deletion: Often called the "right to be forgotten," this is your power to tell a company to permanently erase the personal data it has on you (though there are some exceptions).
Using these rights is a great way to clean up your old data trail. It shrinks your digital footprint and limits how much of your information can be exposed in a future data breach.
How to Make a Data Request
Actually submitting a request is usually pretty simple. Most companies that have to follow laws like Europe’s GDPR or California's CCPA will have a "Privacy" or "Do Not Sell My Personal Information" link tucked away in their website footer. That’s your starting point.
These links usually take you to a form where you can spell out what you want—to see your data, delete it, or opt out of it being sold. You'll have to prove you are who you say you are, which is a good thing. It stops someone else from trying to mess with your information.
What if there's no obvious form? A simple, polite email to their support or privacy contact usually does the trick. Just state clearly who you are and what right you're using. Something like, "Under my rights in the CCPA, I am requesting a copy of all personal data you have about me," works perfectly.
This global shift toward data privacy isn't slowing down. In fact, it's predicted that 75% of the global population will soon have their personal data covered by privacy regulations. With over 160 privacy laws already on the books worldwide, your ability to control your data has never been stronger. You can see more fascinating details in these global data privacy statistics on secureframe.com.
When you use these legal tools, you stop being a passive subject of data collection and become an active participant in your own privacy. It’s about telling companies—on your terms—what they can and can’t do with your information.
Got Lingering Questions? Let's Clear Them Up
Even after you've put in the work, a few questions always seem to pop up. That's completely normal. Learning how to protect your personal information isn't a "set it and forget it" task—it's an ongoing practice.
Think of this section as the final piece of the puzzle. We'll tackle some of the most common concerns and "what-ifs" that people have once they start taking their privacy seriously.
What's the Single Best First Step I Can Take?
If you're looking for the one action with the biggest security payoff, the answer is simple: enable two-factor authentication (2FA) on your critical accounts.
A strong password is your front door lock, but 2FA is the deadbolt. Even if a hacker gets your password from a data breach—which happens all the time—they still can't get into your account. Without that second code from your phone or an authenticator app, they're stopped cold. It's the single most effective way to shut down the vast majority of account takeover attempts.
Do I Really Need a Different Password for Everything?
Yes. One hundred percent. Using the same password across multiple sites is one of the most dangerous and common mistakes you can make.
Here’s why: when a service you use gets hacked, criminals take that list of leaked emails and passwords and immediately try them on other popular sites. This is called "credential stuffing," and it's an automated process. They're banking on you reusing that password for your email, your bank, or your social media.
A unique password for every account contains the damage. A breach at one company won't cascade into a full-blown compromise of your entire digital life. A password manager makes this not just possible, but easy.
Using a password manager is like giving every door in your life a unique, unpickable lock, but you only have to carry one master key. It's the best combination of high security and practical convenience.
How Can I Stop All This Spam and Unwanted Contact?
Feeling overwhelmed by junk mail and robocalls? The best way to regain control is to be more deliberate about who gets your contact information in the first place.
Here are a few practical habits that make a huge difference:
- Use a "burner" email: Set up a secondary email address for things like newsletters, store loyalty programs, and one-off online purchases. This keeps your main inbox clean and reserved for people and services you actually trust.
- Always uncheck the box: When signing up for anything, slow down and look for those pre-checked boxes that opt you into marketing emails. Always uncheck them before you proceed.
- Get on the list: In the U.S., add your phone number to the National Do Not Call Registry. It won't stop illegal scammers, but it will cut down on calls from legitimate telemarketers.
- Tell data brokers to back off: You have the right to tell data brokers—the companies that buy and sell your information—to remove you from their lists. This takes a bit of effort, but it can dramatically reduce junk mail and unsolicited calls over time.
These small steps help you claw back control over who can reach you, cutting down on daily annoyances and your exposure to potential scams.
Trying to make sense of privacy policies and terms of service can feel impossible. TermsEx uses AI to instantly analyze and summarize those long legal documents, flagging key risks and unfair clauses in plain English. Before you click "agree," find out what you're really signing up for.